#get rid of browser hijacker
Explore tagged Tumblr posts
Text
Also checkout latest threats in 2024 onwards Before, cyber attacks were isolated incidents concocted by individuals with a talent for bypassing digital security and hacking personal devices, networks, and small business information systems. Now, it’s a completely different threat landscape, with cyber attacks occasionally being state-sponsored. That means more access to resources and training that’s fully backed by the power of an entire government. And for private sectors, the attacks are getting even more sophisticated as time goes by. Clearly, no business is completely safe from being targeted by a cyber attack. Which is why it’s crucial for all entrepreneurs to know which types of cyber attacks are increasing in trend in order to better protect their assets and reduce any form of compromise. The Biggest Cybersecurity Threats To Watch Out For Phishing The rise of electronic mail, or email, has also marked the start of one of the oldest forms of cyber attacks dating back to the 1990s: phishing. And you can bet that it’s even more widespread and relentless today, involving increasingly sophisticated techniques to get users to click on links or download attachments that contain malware or links to information-capture sites. Common features of phishing emails: Offers something too good to be true They tell you to ask fast (within minutes usually) Includes hyperlinks Contains misspellings in the URL of large company names that can be easy to miss (www.bankofarnerica.com instead of ‘america’) Suspicious (or even unsuspicious) sender Ransomware With different strains discovered every week, ransomware would be among the most dangerous cybersecurity threats of all. From WannaCry, BadRabbit, to NotPetya, this different ransomware wreaked havoc last 2017 by quickly spreading into the network of companies both small and large. And how they work is sinister. Essentially, ransomware restricts access to a device or software unless the target company or individual pays a certain amount of money. The Below Chart Shows The Global Number Of Ransomware Attacks From 2014 All The Way To 2017 One of the best things to do is to consult with an outsourced DPO about backing up your data, get an anti-ransomware application, or turn off your Internet connection as soon as you suspect something suspicious happening to your device. The last option won’t get rid of it, but it can interrupt the ransomware as it tries to finish its encryption, making the infiltration less serious. Cryptojacking The value of cryptocurrencies like Ethereum and Bitcoin gave rise to a new form of the hijacking: cryptojacking. With the focus more centered on Initial Coin Offering (ICO), the losses individuals and companies face are within the millions. And cybersecurity companies have traced that most of these incidents were caused by malware specifically designed for the purpose of stealing cryptocurrencies. Some websites have also fallen victim to this cryptocurrency-centered hijacking. Through mostly undetected script, site visitors were unknowingly letting their devices be used for coin mining on these affected websites. For users, we highly suggest installing an anti-cryptomining extension on your browsers such as No Coin and MinerBlock. And for businesses, the best method to prevent crypto jacking is to have a trained team whose job is to look for cryptomining software or script. The Weaponization of Artificial Intelligence While there’s clearly a place for machine learning and AI in cybersecurity, research is now showing that AI may end up becoming the threat, too. In a report detailing the possible threat of AI, the concerns proposed seem plausible. We’ve created a self-learning machine with the power to take over much of our technological processes. Imagine if attackers were to exploit vulnerabilities in the said AI. We can expect the scope and efficacy of these infiltrations to be increased, making it a more serious threat to cybersecurity, and with larger implications.
Cyber-Physical Attacks Before, it would have been difficult to imagine how a cyberattack could cause potential damages to physical infrastructures. Now, however, it’s as real a threat as any. Let’s not forget about how, between 2008 and 2010, the Stuxnet virus managed to destroy 20% of Iran’s centrifuges by causing them to spin out of control. The same virus then led to the destruction of a blast furnace owned by a German steel mill, adding to the terrifying reality of these cyber-physical attacks. And then there was the recent attack on Ukraine’s power grid that sent the country back to the dark ages. It was believed to be caused by a malware called Industry. As its name suggests, this malware may be among the biggest threats to industrial business networks since the Stuxnet incident. It also sheds light on the ever-growing threat of cyber-physical attacks, which is expected to become even more serious as time passes. Malvertising As businesses, we understand the power advertising has on getting people to take action. Unfortunately, cyber attackers know this too. They’ve now found a way to create highly-convincing advertising material that’s injected with malware and placed them in advertising networks and websites for unsuspecting site visitors. It’s a fairly new concept of spreading malware, but experts agree that they’ll be seeing more of it within the year since the identities of those responsible for the malvertising are often difficult to trace. What You Can Do There may never be a way to completely protect your business from every form of cyber attack, but there are ways for you to be better prepared and set up a better defense system against it, such as the suggestions below: Create a continuous cyber security assessment process. Make security awareness a part of your business’ natural mentality. Always make an assessment of your organization’s security strengths and weaknesses. With how our technology is evolving, we can expect to see scarier and more sophisticated cyber network threats in the next few years. The good news is that our security measures will also continue to evolve to better prepare individuals and organizations for such threats. What matters is that we remain adaptive to this data-driven environment if we want our businesses to survive and thrive. About Author Paul lives and breathes writing. He writes about marketing, business, sports, cybersecurity, or just about anything and everything under the sun.
0 notes
Text
Ever wondered what would happen if your computer got a virus? In today's digital world, it's crucial to know how to fight threats to keep your PC safe. Dealing with adware or ransomware attacks is serious business. This article will show you how to remove viruses and prevent future ones.With over 27 billion searches for virus removal, many are looking for solid solutions1. Losing data or having a slow computer can be a big problem. We're here to help you find the best ways to protect your computer. You won't have to face this alone; we'll guide you to safe and affordable options.Key Takeaways Understanding the different types of malware is essential in ensuring effective virus protection. Regular virus scans can identify threats early and help prevent data loss. Using trusted antivirus software is a vital step in maintaining system performance. A proactive approach can save you from costly repairs in the long run. Involving professionals can provide peace of mind and thorough protection. Understanding Computer VirusesIn today's digital world, it's vital to know about computer viruses to protect our devices. A computer virus is a harmful software that spreads and harms other devices. Spotting infection signs early helps us protect our devices well.What is a Computer Virus?A computer virus attaches to good software and runs without our okay. This can slow down our devices or even cause data loss2.Types of MalwareKnowing about malware types is important. Ransomware, Trojans, and worms are some harmful programs. They aim to harm or break security. Most often, they spread through infected emails3. Malware Browser hijacking Ransomware Resident virus Trojans Web-scripting virus Worms Signs of InfectionIt's key to spot infection signs quickly. Slow performance or strange system messages mean trouble. Viruses can cause browser issues, send out lots of emails, and change passwords. Knowing these signs helps us act fast and avoid bigger problems.https://www.youtube.com/watch?v=BsnHFZun0oUThe Importance of Computer Virus RemovalIt's crucial to remove computer viruses quickly. If we don't, we risk losing data and slowing down our systems. This shows how important removing viruses is for our online safety.Preventing Data LossKeeping our data safe is key in today's digital world. Viruses can destroy or delete files, making them gone for good. We need to scan regularly and remove viruses fast to protect our data. Using strong antivirus software helps fight malware and keeps our data safe showing why removing viruses is vital4.Maintaining System PerformanceViruses also slow down our computers. If your computer is running slow, it might be infected4. Infected systems crash and freeze, making simple tasks hard. Keeping our antivirus software updated helps avoid these problems5. Regular checks and removing viruses keep our devices fast and efficient, helping us use technology better.Common Methods for Computer Virus RemovalIn today's digital world, it's key to know how to remove computer viruses. We have two main ways to do this: using antivirus software or manual methods. Each method has its own benefits, helping us fight malware effectively.Using Antivirus SoftwareUsing antivirus software is a top way to get rid of viruses. Programs like Bitdefender and Norton do automated scans and protect us in real-time. They keep up with new threats by updating often. It's vital to update our antivirus regularly to protect against new malware6. Running scans in Safe Mode helps these tools work better, as it reduces malware interference during removal7.Manual Virus Removal TechniquesAt times, we need to use manual virus removal methods. This means finding and deleting suspicious files ourselves, which can be tricky. We must avoid deleting important system files. First, we should turn off our internet to stop malware from spreading6. Good online habits, like avoiding dodgy emails and links, can also lower the risk of getting infected8. If we're unsure about removing
viruses or if malware is tough, getting expert help or reinstalling our system might be needed8. Method Advantages Considerations Antivirus Software Automated protection and updates May not detect all threats initially Manual Removal Direct control over files Risk of deleting essential system files By using both methods, we can boost our computer's security and tackle malware effectively. For more detailed advice on removing viruses, check out this guide678.Professional Virus Removal ServicesDealing with computer viruses can be tough. That's why getting help from experts is key. We use digital devices more and more, making us more likely to face these threats. So, we need good solutions.Benefits of Hiring Virus Removal ExpertsExperts in virus removal take great care of your system. They know a lot and have the right tools to fix even tough infections. Catching viruses early is crucial. Quick action helps avoid losing files and data9.These pros use special software to get rid of viruses, spyware, and rootkits completely. This keeps your system safe from future problems9.Affordable Virus Removal OptionsFinding affordable virus removal is important for everyone. Cyber threats are getting more complex. We have many services to choose from, fitting different budgets without losing quality.Many companies offer good prices. This lets us get expert help without spending too much. For example, Gadget Kings gives us great service at good prices. They make sure our devices work well again.https://www.youtube.com/watch?v=9hWwY8Lo4agChoosing the Best Virus Removal ServicesChoosing the right virus removal services is key to keeping our devices safe. We should look for companies with a good reputation for effective solutions. Checking user ratings and reviews helps us find these trusted services.Identifying Top-Rated Virus Removal CompaniesTop companies are open about their processes and promise to remove malware. For example, Buzz A Geek has over 300 technicians ready to help across Australia. They offer same-day service without extra fees, aiming for 100% customer satisfaction10. It's important to pick a company with a solid history and meets our needs.What to Expect from Quick Virus Removal ServicesQuick services mean less disruption to our day. Experts do full checks, remove malware, and update our systems. This helps stop permanent damage to our devices11. After the service, we get help with updates to keep our systems safe. This stops future problems. Remember, we can easily contact top companies like Buzz A Geek at 1300 738 570 for quick help10. Service Provider Features Contact Buzz A Geek Same-day service, nationwide support, guaranteed removal 1300 738 570 McAfee Comprehensive security features, frequent updates Visit Site Norton Identity theft protection, bundled services Visit Site AVG Reliable free antivirus, strong malware protection Visit Site 10Do-It-Yourself Computer Virus RemovalStarting to remove viruses on your own can be empowering, but we must be careful. First, make sure your system is well-protected. Enable Microsoft Defender and Windows Firewall to defend against threats. Then, we can look into ways to remove viruses and take back control.Initial Steps for DIY RemovalFirst, spot signs of a virus infection. Look for a slow computer, slow apps, and more popup ads than usual. Also, check for unwanted programs running at startup and sudden screen freezes. Some viruses can spread and be hard to remove, so starting right is key12.Here are the first steps for removing viruses yourself: Enable Microsoft Defender and Windows Firewall. Run a Boot-time Scan in Safe Mode, usually taking just a few minutes to complete13. Use trusted antivirus software to find and remove threats. Do a Disk Cleanup to free space and possibly fix some issues13. Remember, spyware can hide deep in our systems. It's hard to spot or remove, showing the importance of strong protection and careful steps throughout12.For more help on removing viruses, check out guides for Mac and PC.
These can help us deal with infections here12.Prevention Strategies Against Computer VirusesIn our quest for better computer security, we must use strong virus prevention strategies. Keeping our software updated and using antivirus solutions is key to securing your computer. With most malware not being pure viruses, staying alert and proactive is vital14. Regular updates to antivirus software and weekly scans can greatly lower the risk of new viruses14.Be careful with email attachments, as they often spread viruses15. Using strong firewalls and antivirus can block most threats15. Make sure your passwords are complex and change them often to fight against brute force attacks16.Teaching employees about cybersecurity risks is crucial in fighting computer viruses. Most breaches happen because of human mistakes14. Learning to spot phishing attacks and avoid dangerous links helps us stay safe. With so many web pages online, staying alert is key14.By following these steps, we can build a strong defence against threats. These actions will keep our data safe. For more tips on securing your computer, check out this source. Strategy Description Importance Regular Software Updates Keep your software and operating systems up to date with the latest patches. Helps close security gaps and vulnerabilities. Antivirus Scans Conduct daily or weekly scans to detect and remove threats. Prevents the spread of malware in your system. Secure Passwords Create complex passwords and change them regularly. Reduces the risk of unauthorized access. Employee Education Train staff on the importance of cybersecurity practices. Minimizes human errors leading to security breaches. Virus Removal Near Me: Finding Local HelpWhen we look for virus removal near me, it's key to find trustworthy local experts. They should know our specific needs. There are many ways to help us find the right people, and knowing what to look for saves time and keeps our devices safe.How to Locate Trusted Virus Removal SpecialistsTo find good local virus removal experts, follow these steps: Look up local businesses that remove viruses, like Geeks2U. They offer computer repair services all over Australia and can help on the same day.Learn more about their services.17 Check out what customers say. Some services have a perfect 5/5 rating from 290 reviews, showing they're really good18. See what services they offer, like finding problems, removing malware, and installing software. Get in touch with them to see how fast they respond, with many offering quick help through online forms. Local Virus Removal RatesIt's important to know what virus removal costs locally. Prices change a lot between services. This depends on where you are, how hard the problem is, and how skilled they are: Service Provider Typical Rates (AUD) Services Offered Geeks2U $99 - $180 Virus removal, repairs, and software help Trade Computers $75 - $150 Virus removal, protection, and checks Bowe's I.T. Solutions $70 - $130 Virus removal and network setup PC Daddy $80 - $140 Laptop and desktop fixes, virus removal Prices can change based on what you need and the local market. Doing some research helps us find local virus removal specialists who know their stuff and charge fair prices.By being careful and thorough in our search, we can keep our digital world safe and our devices running well171819.ConclusionIn this guide, we've looked at how to remove computer viruses and keep our PCs safe. Computer viruses can cause a lot of damage, costing billions of dollars each year20. It's important to stay careful online, whether you use experts or try to fix things yourself. Being proactive helps protect your PC.We talked about different types of computer threats, like boot sector viruses and direct action viruses. These can spread through emails and downloads21. Knowing about these threats shows why it's crucial to back up your data and use the latest antivirus software.At the end, we see that using different ways to prevent viruses and understanding them helps us stay safe online.
For extra help, think about using services that focus on virus removal and fixing computers. This can include experts like those at Gadget Kings.FAQWhat is a computer virus?A computer virus is a harmful software that spreads and copies itself. It can damage your systems and data.How can I tell if my computer has a virus?Look out for signs like software crashing, slow performance, and pop-ups. Unusual system messages can also indicate an infection.What are the best methods for computer virus removal?Use antivirus software like Bitdefender or Norton for protection. Or, manually delete suspect files if you know what you're doing.Should I hire professionals for virus removal?Yes, experts are best for serious infections. They have the right tools and knowledge to fix complex problems safely.What are affordable options for professional virus removal?Affordable services are available that offer effective help without breaking the bank. This makes expert assistance available to everyone.How do I find top-rated virus removal companies?Check online for user reviews and ratings. Choose a company with a good reputation and clear processes and guarantees.What can I expect from quick virus removal services?Quick services aim to fix problems fast with little disruption. They help you get back to normal quickly.What initial steps should I take for do-it-yourself virus removal?First, make sure your system is safe by turning on Microsoft Defender and Windows Firewall. Then, carefully identify and delete any suspicious files.How can I prevent future virus infections?Keep your software updated, use antivirus solutions, and be careful with emails and links. These steps will help protect your computer.How can I find local virus removal specialists near me?Search online, read local reviews, and compare services to find trusted specialists in your area.What are typical local virus removal rates?Prices vary by service complexity. Research different providers to understand the average costs for their services. Source Links How to Get Rid of a Virus & Other Malware on Your Computer - https://www.avg.com/en/signal/how-to-get-rid-of-a-virus-or-malware-on-your-computer Our complete guide to computer viruses - https://www.buzzageek.com.au/our-complete-guide-to-computer-viruses/ What Is A Computer Virus? Virus - https://www.webroot.com/us/en/resources/tips-articles/computer-security-threats-computer-viruses How to Wipe Out a Computer Virus | McAfee - https://www.mcafee.com/learn/how-to-wipe-out-a-computer-virus/ What is Virus Removal | How to Remove Virus from Your PC - https://www.xcitium.com/blog/pc-security/what-is-virus-removal/ How to remove a virus from computer in 2024 - https://www.malwarebytes.com/cybersecurity/basics/how-to-remove-virus-from-computer How to Get Rid of a Virus on a Windows PC - https://electronics.howstuffworks.com/how-to-tech/how-to-remove-computer-virus.htm How to remove malware from a Mac or PC - Norton - https://us.norton.com/blog/malware/how-to-remove-malware Computer Repairs - https://www.geeks2u.com.au/virus-spyware-malware-removal/ Virus, Spyware, Malware & Ransomware Removal Support Services - https://www.buzzageek.com.au/virus-spyware-malware-removal/ Virus Removal, Spyware & Malware Removal - https://www.peelcomputers.com.au/products/virus-removal-spyware-malware-removal Computer Virus Removal | Crypto Virus Removal - Spyware Protection - https://mobilecomputers.com.au/computer-viruses-removal/ How to Get Rid of Viruses and Other Malware From Your Computer - https://www.avast.com/c-how-to-remove-virus-from-pc 7 Tips on How to Prevent Computer Viruses From Infiltrating Your Network - https://resources.xceptional.com/blog/7-tips-on-how-to-prevent-computer-viruses-2 How to Protect Computer from Viruses - https://www.chicagoitsolutions.com/2022/07/22/11-ways-to-protect-your-computer-from-viruses/ 10 Ways to Help Protect Your Computer Network from Viruses and Attacks - https://www.claconnect.com/en/resources/articles/2021/10-ways-to-help-protect-your-computer-network-from-viruses-and-attacks
Computer Repairs - https://www.geeks2u.com.au/computer-repairs Virus, Spyware & Malware Removal Melbourne | Computer Cures - https://computercures.com.au/virus-spyware-malware-removal/ 10 BEST Computer Virus Removal in Newcastle NSW | Localsearch - https://www.localsearch.com.au/find/computer-virus-removal/newcastle-nsw Computer virus - https://en.wikipedia.org/wiki/Computer_virus What is a Computer Virus? - https://friendlycaptcha.com/wiki/what-is-a-computer-virus/
0 notes
Text
I have been hijacked by Your Search Bar malware... T_T
Google Chrome had just been invaded by Your Search Bar malware virus. It was installed without me knowing and I had to go through the similar steps to getting rid of it.
If you find it.
Do the uninstalling here.
securedstatus.comRemove Your Search Bar Browser Hijacker Virus (Step-by-Step Guide) - SecuredStatus
Important details about Your Search Bar Your Search Bar is a malicious extension for Google Chrome and other web browsers. It has the ability to adjust your browser’s settings, including […]
Oh how I love hijackers....

0 notes
Text
Computer virus for software
Computer Virus Definition
Computer virus is a part of software, virus effect the system software and the other function of computer, whereas the computer navigation may be slow, and also causes virus spread among computer and software as well as data.
Virus always targets disrupt system effect the massive operational issues If virus spreads in your software program, then the system loss the data and also work will slow. The major thing to know about computer viruses is that these are designed to spreads over the programs and software systems. When the virus comes in your system via unknown thing using which can damage your document or software that is attached to via networks, file sending and sharing or as well as email attachments.
Speed Of System
Due to virus the user cannot smoothly navigate the system because when system would have virus so then system running slower and unwilling your application and internet as well as your software runs slow.
Windows Pop-Up
Unwelcome pop-up reaching on a computer or web browser indicator signs of a computer virus. Unwelcome pop-up sign indicate the malware, viruses, or spyware damaging a device.
Crashes Device
Unwillingly system crashes and damages the computer itself surprisingly closing down are basic indicators of a virus. Due to computer viruses, computer to perform in a variety of different way.
Accounts Being Logged Out
Some viruses are meant to target particular programs, either crashing them or making the user automatically log out of the service.
Sending Bulk Emails From Your Email Account
Email is frequently used to propagate computer viruses. Hackers can spread viruses and conduct larger cyberattacks via other people's email accounts.
Your Homepage Might Change
Any unanticipated alterations to a computer, such as changing your system's homepage or updating any browser settings, are indicators that a virus may be present on the device.
Why Do Computer Viruses Attack and Damage?
In the early beginning of Computers, Viruses are spreading between devices and software, as we are seeing that nowadays, Viruses can however be spread via hard disks and others thing.
Computer Viruses types
Devices can become infected by a variety of computer viruses. The prevention of computer viruses and methods for getting rid of them are covered in this section.
Resident Virus
The way viruses spread is through infecting host computer software. By infecting apps as they are opened by a user, a resident virus does this.
Specific Action
A direct action virus gains access to the system's main memory and corrupts all of the files, folders, and programs found in the autoexec.bat path before erasing itself.
Multipartite Virus
A multipartite virus infects and spreads across computers using a variety of strategies. Usually, it stays in the computer's memory until it infects the hard drive.
Browser Hijecker
An application called a "browser hijacker" alters the default settings of online browsers, such as the homepage, new tab page, and default search engine.
Overwrite Virus
Overwrite viruses are incredibly harmful. Data can be deleted, and new code or file content can be added in its place.
0 notes
Text
How to remove Yahoo Search Redirect from your system?
Cyber security analysts have recently discovered that Yahoo Search Engine is being utilized by the cyber-criminals to generate illicit revenue by driving searches to search.yahoo.com. While Yahoo Search is a legitimate search provider, cyber threat-actors are able to succeed in their deceitful motives with the help of nasty browser hijackers.

These browser hijackers such as oursurfing, istartsurf & istart123 cause Yahoo Search Direct i.e. it diverts the web-searches to search.yahoo.com without user’s consent. Software Bundling is known to be the prime method of its distribution.
Once the system is infected, the browser hijacker changes the new tab functionality, home-page & default search engine settings without user’s permission. The altered settings are assigned to Yahoo Search Engine. In addition to that, the malware installs certain applications named as “helper objects” on the infected system that prevents the user from restoring the default settings.
How to remove yahoo search redirect
#yahoo search redirect#yahoo search virus Mac#get rid of browser hijacker#remove Yahoo search redirect#Yahoo search redirect removal
0 notes
Text
oh lovely now my laptop has a virus
#why#cant go to the mall to fix it either!!!!#i knew something has been wonky lately...#it's the search browser and i looked it up and it's a hijack browser and idk how to get rid of it...
3 notes
·
View notes
Text
tumblr i gotta be honest making video ads hijack my phone’s audio and play even when my phone is muted will not drive me to pay to get rid of ads. it will actually make me delete the app and go back to using the mobile browser version
20 notes
·
View notes
Link
#remove browser hijacker biglocateriod.pro firefox#How to remove Biglocateriod.pro hijacker#delete Biglocateriod.pro hijacker from PC#get rid of Biglocateriod.pro hijacker
0 notes
Link
#uninstall browser redirect virus#Browser Redirect Virus#Browser Redirect#Remove Browser Redirect Virus#Delete Browser Redirect Virus#Get rid of Browser Redirect Virus#Eliminate Browser Redirect Virus#Block Browser Redirect Virus#Browser Redirect Virus removal#How to delete Browser Redirect Virus#How to remove Browser Redirect Virus#browser redirect virus mac#browser redirect virus android#browser redirect virus chrome#how do i stop a redirect on browser?#when i click on a website it redirects me somewhere else#how to remove redirect virus from windows 10#browser hijacker virus#browser hijacker removal tool
0 notes
Text
How does Malware Works
Malware is short for malicious software. It is also referred to as spyware. Malware is software that has been designed specifically to disrupt someone's computer. A Trojan horse, a virus or a worm could be classified as malware. Some of the advertising software that is out there can be considered malware because it attempts to re-install itself after you get rid of it.
Explaining Malicious Software (Malware)
Malware is software designed to cause harm to a computer and user. Some forms of malware “spy” on user Internet traffic. Examples include spyware and adware. Spyware monitors a user’s location and if enabled, it can capture sensitive information, e.g., credit card numbers, promoting identity theft. Adware also acquires user information, which is shared with advertisers and then integrated with unwanted, triggered pop-up ads.
Worms and viruses behave differently, as they can quickly proliferate and undermine an entire computer system. They also may perform unsavory activities from a user’s computer without the user’s knowledge. In the wake of a virus or worm, a computer system can experience significant damage.
Anti-malware should determine if there are threats by scanning a computer and removing them, if found. Prevention is better than corrective action after infection. Although anti-virus programs should be continually enabled and updated, certain types of threats, like spyware, often make their way into a computer system....get more to know at - techopedia.com.

How Malware Works
Malware authors use a variety of physical and virtual means to spread malware that infect devices and networks. For example, malicious programs can be delivered to a system with a USB drive or can spread over the internet through drive-by downloads, which automatically download malicious programs to systems without the user's approval or knowledge. Phishing attacks are another common type of malware delivery where emails disguised as legitimate messages contain malicious links or attachments that can deliver the malware executable to unsuspecting users. Sophisticated malware attacks often feature the use of a command-and-control server that allows threat actors to communicate with the infected systems, exfiltrate sensitive data and even remotely control the compromised device or server...find out more at - Techtarget.com.
Common Types of Malware
Though some of these terms can be used to describe software with a legitimate, non-malicious intent, malware is generally understood to exist in one or more of the following forms:
Viruses infect program files and/or personal files.
Spyware collects personal information.
A worm is malware that can replicate and spread itself across a network.
A Trojan horse looks, and may even operate, as a legitimate program.
Browser hijacker is malware that modifies your web browser.
Rootkit grants administrative rights for malicious intent.
Malvertising is malware that uses legitimate online advertising to spread malicious software.
To know more, visit - Lifewire.

Growing Risk
The risks posed by malicious code are on the rise, due to fundamental changes in the threats and purposes that malicious code is put to. Instead of just causing a nuisance and being destructive, malicious code attacks are becoming more motivated by financial gain. Attackers are increasingly sophisticated and organised, adopting methods that are similar to traditional software development and business practices.
It has been shown that the amount of time between the discovery of a software vulnerability and attempts to exploit that vulnerability via attacks from new computer viruses/worms is continuously decreasing. In addition, it takes time for anti-virus vendors to develop virus and malicious code definitions, so there is always a chance that your anti-virus software cannot detect newly discovered malicious code in time. Thus, your computer is still vulnerable to virus attack if other security best practices are not put in place.
Your computer system could be infected if:
a user is lured into installing or opening a malicious attachment / program / plug-in from an untrusted source or from a spam email
a user is lured into visiting a malicious website
the computer is not properly patched, so attackers take advantage and exploit a vulnerability
the computer is not properly configured, so attackers take advantage and exploit a vulnerability
Read more over at - Infosec.
Whether or not you think you may have been infected with malware, it is best to scan your computer regularly for malware threats. Visit - https://www.phishprotection.com/ to know more about malware and how to mitigate against these types of attacks.
1 note
·
View note
Link
SearchesSpace.com is a fake search engine which will make you into believing that it can help you find useful information. In fact it is a browser hijacker that sets itself as your default homepage and search engine. You can’t change your browser settings back until you remove it completely.
#SearchesSpace.com#browser hijacker#remove SearchesSpace.com#get rid of browser hijacker#SearchesSpace.com removal#SearchesSpace virus#SearchesSpace search engine#fake search engine#redirect virus
0 notes
Text
(copy-pasted from discord)
hoo boy i just had a quite unpleasant experience but i THINK/HOPE i got it sorted out
heads up: if you come an anti-virus software (or worse found it already making itself at home in your machine like I did even though you certainly didn't download/install it much less consented to it) called
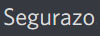
GET RID OF THAT BASTARD
i found some solutions through Reddit, many recommending a program called Malwarebytes. For what it looks like it is a good deal
usually if i find something suspicious in my junkyard of a pc i just delete the whole thing (and force-kill programs in task manager if that's preventing it)
you legit can't force-kill S//egura//zo processes because they'd just keep coming back up and running, which would disable you from deleting the thing due to having processes running
don't bother using its uninstaller, its faker than shadow the hedgehog
chances are it won't do anything and may even cause the bastard to root itself even deeper into your machine like a kid disappearing to the bottom of a ballpit
what i did at least was... after having downloaded malwarebytes i restarted my pc in safe mode (with networking) and ran malwarebytes to scan for threats (make sure its toggled to scan for rootkits too) and while it scanned i manually attempted to track down just about anything that could be that dastardly program, related to it, or from it and deleted it all as well as uninstalling a few 'leftovers' here and there even with my work there malwarebytes picked up about 134 P.U.P.s and one malware. quarantined then deleted all that crap
ofc did more scans after that one and kept looking for undesired crap to get rid of
i even went into Regedit to track and obliterate stuff from Se///gur///az///o there
the dick move of it is that S///eg///ura///zo tries really hard to look like an honest and legit thing, but they usually come hidden in a download you make and installs itself into your machine without your consent and makes just about any ability you have to remove it powerless before its persistence
no legit company will give out copies of their anti-viruses for free as a 'surprise bonus' in seemingly unrelated downloads, especially not programs that arent free trial versions, and no legit anti-virus will install and root itself to your machine without your consent
its a trap and my dumb ass fell for it but i noticed it quickly thanks to chrome pointing out something happened among extensions (it also installed an extension to chrome without any commanded permission from me)
speaking of Chrome, there was also Chromium somewhere along this but that one i got rid of quickly (Chromium itself is a legit thing from Google, it’s their open source for Chrome for people to create their own browsers, but more often than not people use it for malware, usually browser-hijacking)
also as a reassuring note, youre not stupid for falling into something like this (especially if you at least have conscience and try to be as careful as you possibly know how), dishonest people can be really smart and sneaky, and they keep getting smarter, craftier, more creative, like, ugh, bots
even a careful person can fall into one of those eventually
as of right now im running another scan with malwarebytes, just to be sure
#jellycream speaks#psa#reference#technical issues#read more#nowadays you can never be TOO careful with this sort of thing
3 notes
·
View notes
Text
How to remove CalendarSpark Browser Hijacker from your system?
Guide to remove CalendarSpark Browser Hijacker from System
CalendarSpark Browser Hijacker is a dubious toolbar which claims to assist users. with a simple calendar to plan out their daily activities. Superficially, CalendarSpark Extension might look like a genuine tool, But, internally it has the ability to make harmful changes to your browser.

This rogue browser extension comes under the category of Potentially Unwanted Program (PUP) & browser hijacker. CalendarSpark Browser Hijacker spreads via Software bundling & its official Website. 3 primary reasons to designate CalendarSpark as a browser hijacker are: Alteration of browser settings, Web browser activity tracking & Stealth installation.
Read Full Article
#CalendarSpark removal instructions#CalendarSpark browser hijacker#CalendarSpark browser hijacker removal#CalendarSpark Extension#remove CalendarSpark#get rid of CalendarSpark#CalendarSpark removal guide#uninstall calenderspark#CalendarSpark removal
0 notes
Text
lost xkit when i wiped my browser cuz of the hijacker thing and now tumblr is literally so annoying.. all these random recommended blogs popping up on my dash i cant get rid of, cant add tags to my posts unless i go into the post itself, cant see tags anymore... i hate it
1 note
·
View note
Text
Streameast Live
However, you should safeguard yourself from spyware and spies if you are streaming online. It entails setting up an antivirus program to guard against viruses and a VPN to secure your data and maintain your anonymity.
Using a VPN will make you anonymous online, but this is no justification for breaking the law. Additionally, although though VPN use is normally permitted, certain nations forbid it. As a result, if you are unclear, we encourage you to follow the local laws.
Utilizing StreamEast has risks.
Free streaming services are becoming more and more popular, but are they secure? To maintain security on StreamEast, you need first ask yourself that question.
First off, as was already established, certain nations consider using free streaming websites to be unlawful. You could therefore face arrest or a severe fine.
Second, many free streaming services lack adequate security, including StreamEast. You could therefore easily become a victim of hacking or worse.
Thirdly, a lot of free streaming websites are infected with spyware and the dreaded ransomware. They can jeopardize your personal information or hijack your machine while disguising themselves as adverts.
The practice of cloning, often known as mirror sites, is a significant problem with well-known free streaming websites like StreamEast. They are produced and maintained by independent parties who are not connected to the original website. Unfortunately, there are a lot of websites, and it can be difficult to tell which ones are reliable.

Beware of mirror websites
Mirror sites have the drawback that they might be used by unscrupulous actors to track your data or infect your device with malware. Additionally, because they are restarted online after being shut down under a different name, authorities cannot control them.
How can I get rid of a virus from StreamEast or one of its mirrors if it infects my computer?
The majority of StreamEast's viruses are distributed by push notifications, pop-up windows, and unapproved advertisements, all of which are difficult to ignore. When you click on them, your computer can download malicious software or be redirected to questionable websites.
Even if you exercise extreme caution, it's nearly impossible to avoid becoming infected due to the never-ending barrage of pop-ups and advertisements. For instance, clicking inadvertently on the incorrect area of the homepage could result in the automated installation of malicious software.
Additionally, some advertising will make an effort to con you by requesting that you download cleaners in order to get rid of infections from your device. Installing the cleaning, however, will have the opposite effect and infect your device with a virus. Additionally, it can jeopardize the security of your device and cause annoying pop-ups to appear everywhere.
To make matters worse, spyware on StreamEast and its mirrors might take a variety of shapes. As a result, the following are typical signs that your device been infected while you were viewing StreamEast:
Default search engine that is unnamed
Your browser has probably been taken over if you open it and see a strange new default search engine. Your device may have been infected with StreamEast malware, which was designed to gather data and your personal information.
Can I really stay secure on StreamEast with a VPN?
Using free streaming services like StreamEast is risky, as you can see from the information above. You can, however, take security measures to keep utilizing these sites. Utilizing a Virtual Private Network (VPN) is the most effective technique to secure your online connections.
Our best suggestions provide top-notch encryption to guard against unauthorized access to the data carried across your network. They employ a strong algorithm to ensure that no one can decipher your data.
When watching on free streaming websites like StreamEast, some services, like NordVPN, provide an efficient ad blocker. Additionally, it filters spyware to protect you from viruses from phony streaming services.
In addition to strong encryption and ad/malware blocker, VPNs also have a kill switch. If the VPN is offline, it will disconnect you from the network to keep you private at all times. Additionally, they offer DNS leak defense to stop your DNS request from going through your ISP's servers, which could betray your identity.
A VPN will also enable you to get around geographic limitations and access restricted content on premium websites like Netflix in other locations. Additionally, it is useful for torrenting because it will safeguard your connections when using torrenting websites.
For more information, visit https://streameast.help/.
1 note
·
View note